The dark web monitoring
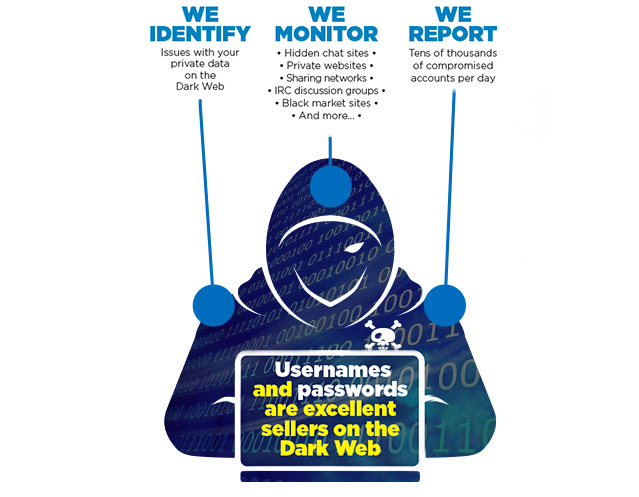
Why remote monitoring of the presence of your information on the dark web is important

Passwords as we know them are solutions to past problems. Nowadays, with the increasing number of services and sites that require a password, we are increasing the risk of using the same password everywhere or variations that are easy to decipher logically or by cross-referencing.

Usernames and passwords are the most wanted by hackers. Those who know how to exploit the weaknesses of the Web and its users can easily infiltrate systems to steal hundreds, or even thousands at a time.

Hackers risk acquiring other victims through your contacts and other privileged documents that they will identify in their research (even take advantage of this to deploy ransomware on your company’s servers after destroying your copies of poorly secured cloud backup).
How is the information compromised?
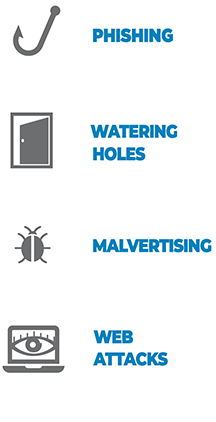
• Emails that seem legitimate
• Attachments / shortcuts with password sensors
• Human engineering
• Infiltration of known service databases
(social media, corporate intranet)
• Injecting malicious code into a legitimate site
• Banner of advertising infected on a legitimate website
• Random scanning of private and public interfaces having Internet access (firewalls, routers, servers) for vulnerabilities
• Exploitation of environmental security vulnerabilities
• Integrated into a Trojan horse (as a secondary or main tool)
in order to inventory passwords
What can a hacker do with your account information?

• Get inspired to try to break into other services with the same access
• Send attacks to your contacts / customers via your email account
• Introduce malicious applications into your environment without your knowledge.
• Extract sensitive information about you and / or your customers
• Steal your identity to access your bank account and / or your credit card
