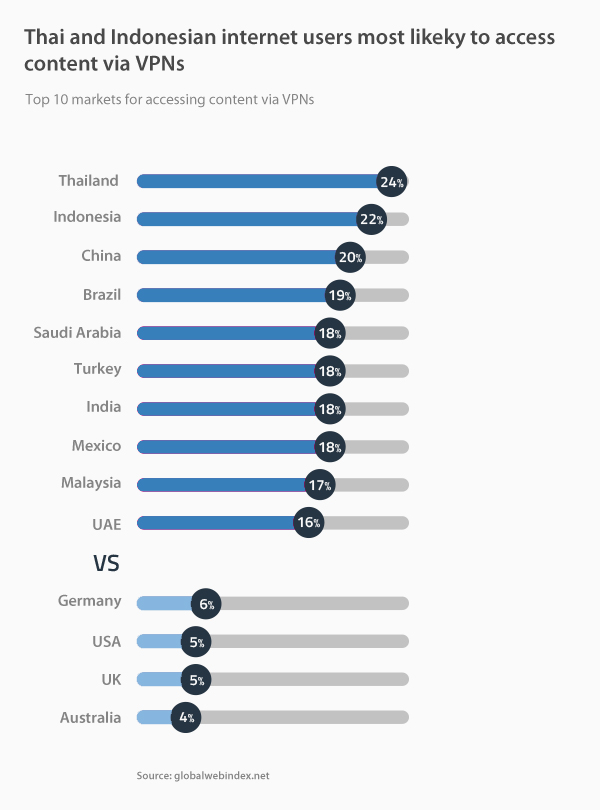
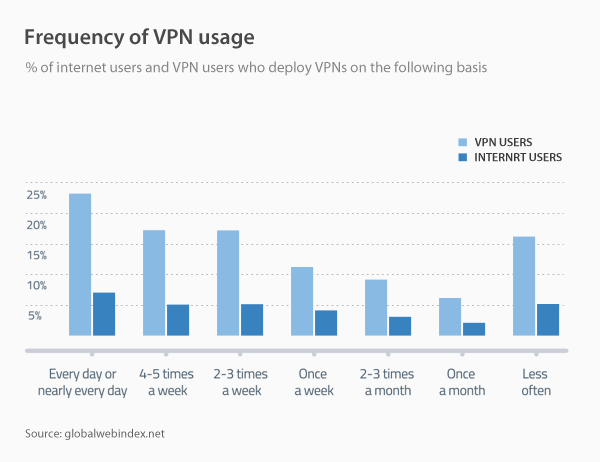
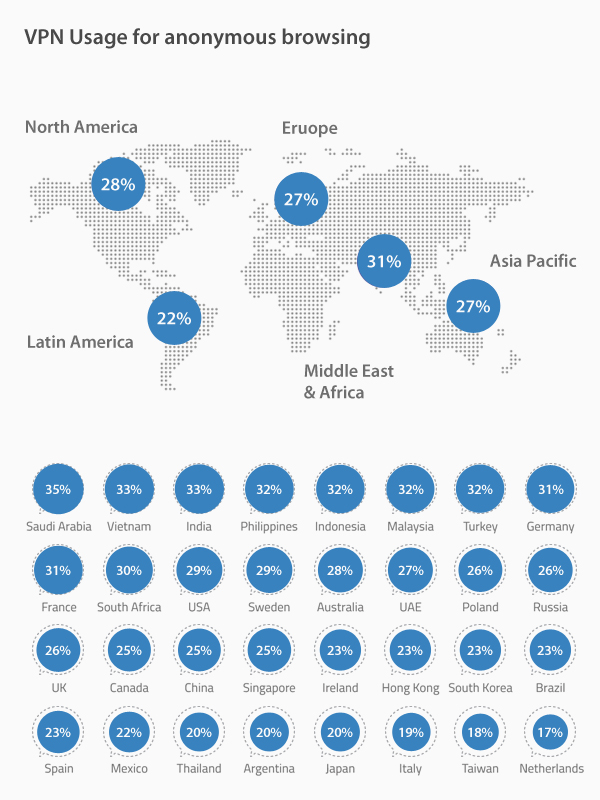
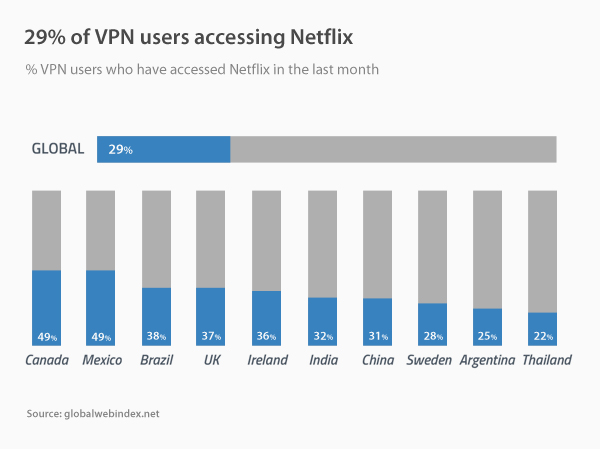
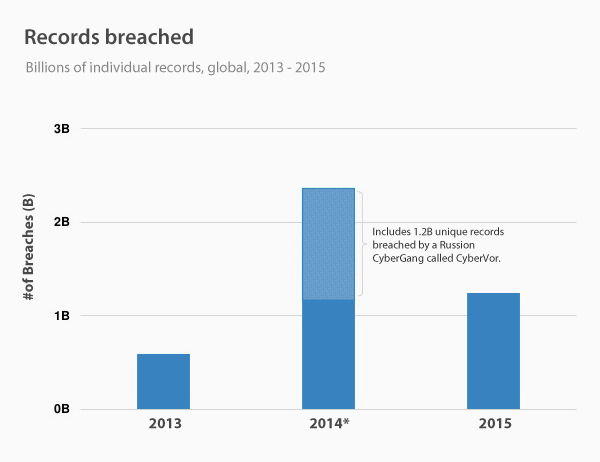
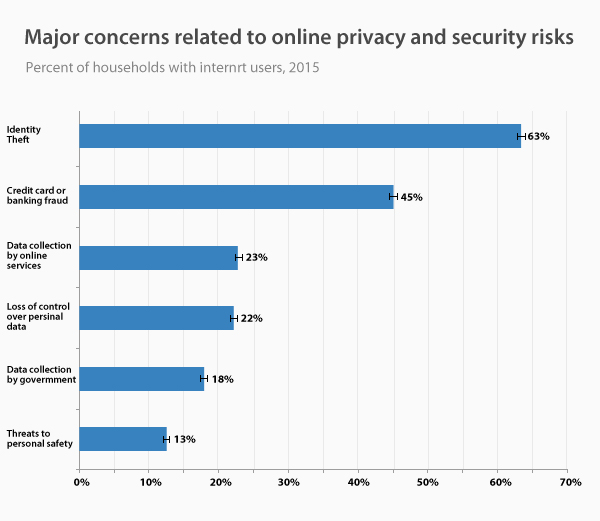
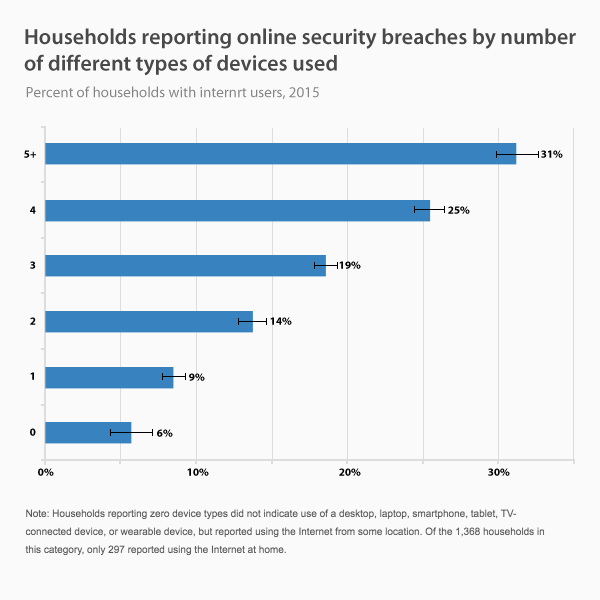
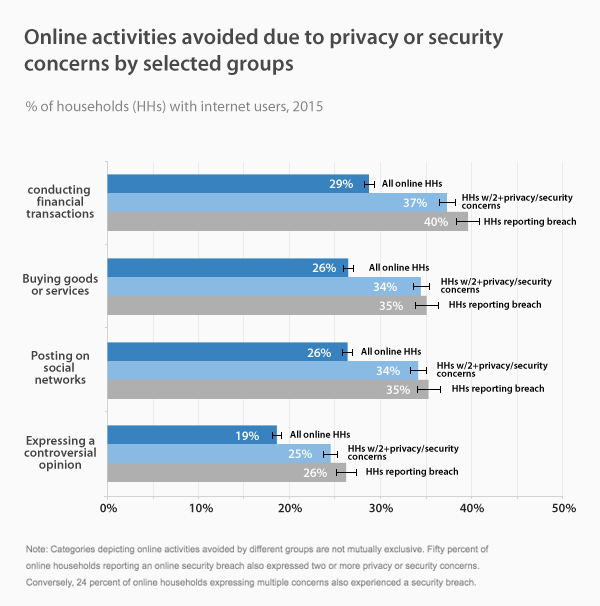
Work from home has become an increasingly popular phenomenon in recent years, offering workers unprecedented flexibility in carrying out their professional tasks. This practice allows employees to work remotely, from home or other locations, using modern communication technologies. However, despite its many benefits, working from home does not come without its share of risks and challenges, especially when it comes to cybersecurity. Indeed, this new way of working exposes companies and workers to potential threats, jeopardizing the confidentiality of sensitive data and the stability of computer systems.

Does working from home pose a cybersecurity risk?
Yes, working from home presents certain cybersecurity risks that companies must deal with. When employees work remotely, they typically use their own home devices and networks, increasing the potential attack surface.
Cybersecurity for remote working is essential to protect sensitive data of companies and individuals. Here are some of the best measures to put in place to ensure the safety of working from home:
- Use a Virtual Private Network (VPN): Employees should use a VPN to access company resources. This encrypts the connection and protects data from prying eyes as it travels over the Internet.
- Multi-Factor Authentication (MFA): Implementing MFA enhances account security by requiring multiple factors of identification, such as password, code generated on a mobile device, or text message.
- Regular Software Updates: Keeping operating systems, applications, and anti-virus software up to date is critical to patching known vulnerabilities.
- Security Awareness: Conduct cybersecurity awareness sessions to educate employees on common threats and security best practices.
- Data Encryption: Encourage or require encryption of sensitive data on employee devices, whether in motion or at rest.
- Clear security policies: Put in place security policies specific to working from home, defining employee responsibilities and restrictions on the use of IT equipment and access to data.
- Privilege-Based Access: Limit access to critical information only to employees who need it to perform their jobs.
- Device security: Deploy mobile device management (MDM) solutions to secure personal devices used for work and be able to erase them remotely in the event of loss or theft.
- Regular backups: Encourage the regular backup of critical data on secure servers, in order to prevent data loss in the event of an incident.
- Make an appointment with a cybersecurity expert: A specialized company like Équipe Microfix can support your business in implementing the best cybersecurity practices.
By adopting these security measures, companies can improve the protection of their data and reduce the risks associated with working from home. It is also important to keep in mind that cybersecurity is an ongoing process, and one should stay up to date on new threats and best practices to ensure effective protection.